1. 典型算法业界要求参考
| 算法 | NIST | BSI | ANSSI |
|---|---|---|---|
| 3DES | 新系统禁止,2023年底前遗留使用 | 新系统禁止,2022年底前遗留使用 | 2020年后不建议使用 |
| HMAC-SHA1 | 允许 | 允许,每年例行审视 | 允许 |
| RSA|DH|DSA(2048bit) | 2030年年底前允许 | 2022年年底前允许2000bit | 2030年年底前允许 |
| ECDH|ECDSA|ECIES(224bit) | 2030年年底前允许 | 2022年年底前允许200bit | 2020年年底允许200bit |
2. NIST官方文档说明
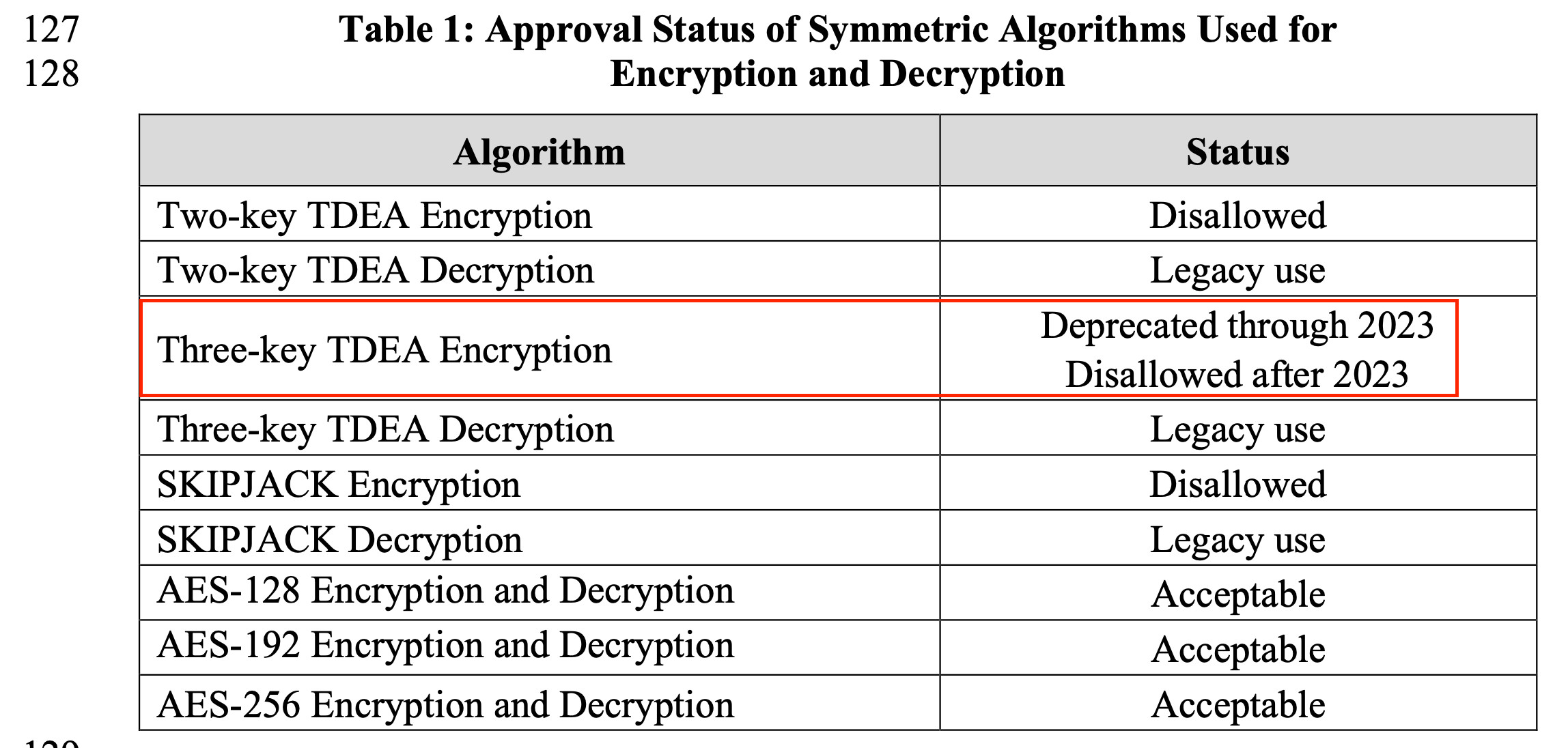
3. 其它参考
3.1. https://www.cryptomathic.com/news-events/blog/3des-is-officially-being-retired
3.1.1. Why 3DES is Likely to Be Disallowed after 2023
3DES is a ciphersuite based on the Data Encryption Standard developed by IBM in the early 1970s and adopted by NIST (with minor changes) in 1977. 3DES was introduced during a period of transition between two major algorithms. In 1997, NIST announced a formal search for candidate algorithms to replace DES. In 2001, AES was released with the intention of coexisting with 3DES until 2030, permitting a gradual transition. However, the retirement of 3DES has been likely accelerated by research which has revealed significant vulnerabilities and is, by some accounts, long overdue.
NIST first initiated discussion of deprecating 3DES following the analysis and demonstration of attacks on 3DES. The Sweet32 vulnerability was made public by researchers Karthikeyan Bhargavan and Gaëtan Leurent. This research exploited a known vulnerability to collision attacks in 3DES and other 64-bit block cipher suites which are greatest during lengthy transmissions, the exchange of content files, or transmissions vulnerable to text injection. After the exposure of this vulnerability, NIST proposed 3DES be deprecated, and soon thereafter, restricted its usage.
3.2. https://csrc.nist.gov/News/2017/Update-to-Current-Use-and-Deprecation-of-TDEA
3.3. https://www.encryptionconsulting.com/why-3des-or-triple-des-is-officially-being-retired
声明:本文采用 BY-NC-SA 协议进行授权 | 星期九
原创文章转载请注明:转自《为什么3DES只能用到2022年底》